The accompanying blog, that forms the notes for this cheat sheet, can be read here.
Adrian Mouat gives an excellent talk called 'Using Docker Safely'. He will do it this Friday at GOTO; Amsterdam. If you get a chance to see it, you should.
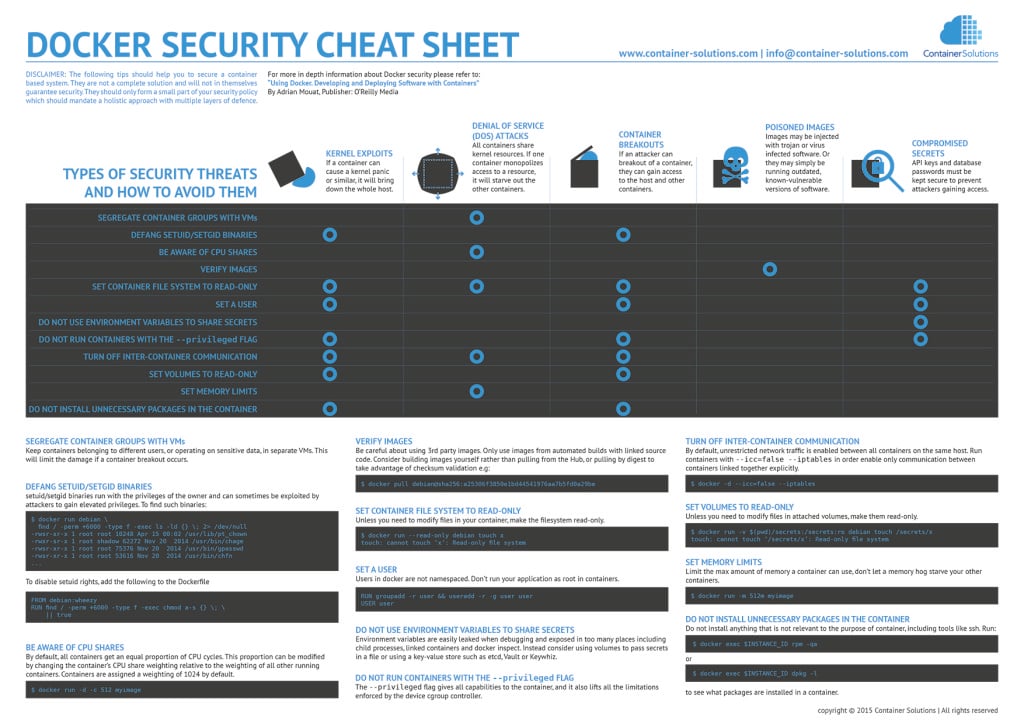
As part of security week, we have summarised Adrian's guidelines onto a cheat sheet, which you can download in high resolution by clicking on the image below. You can also visit us our booth at GOTO; this week and grab a hard copy.


 Previous article
Previous article
